August 17, 2018
Senator Ron Wyden
221 Dirksen Senate Office Bldg.
Washington DC, 20510
Dear Senator Wyden:
We are writing to you regarding our concern that the Chinese government, or Chinese nationalist hackers, may be using the phone networks to monitor and map a wide swathe of people living in the United States, including Tibetans, Chinese democracy activists and other dissidents and people considered ‘opponents’ of the Chinese Communist Party.
In recent months, many Tibetan activists, Chinese dissidents, and other rights advocates have received unsolicited calls and voicemails from numbers that appear to be Chinese consulates in New York City and San Francisco. Though we understand that such calls are considered to be a part of a major international Chinese Robocall scam, the timing and targeting of these specific calls to people in our network, and their relation to a campaign to shut down China’s Confucius Institutes in the U.S., suggests a political link.
As activists with a history of being personally targeted by sophisticated online malware attacks originating from China, including the 2010 attack on Google (1) , and those outlined in the groundbreaking 2007 GhostNet report from the University of Toronto’s Citizen Lab(2), we have reason to believe the “spam” calls we are receiving may not be benign. In fact, we experienced targeted harassment and intimidation from Chinese sources through cell phone networks ten years ago, during the 2008 Olympic torch relay in San Francisco. At that time, you requested the FBI to investigate the barrage of calls, including ghost dialing and verbal abuse delivered live and via voicemail, that targeted those of us involved in organizing protests.
Based on our previous experience, we believe that there is a possible connection between the “spam” calls and the improper sharing of location data (Securus, etc), and flaws in the mobile network infrastructure (SS7) that have recently come to light. When combined, these vulnerabilities could provide a nation-state with advanced capabilities, including targeted harassment, disinformation, malware delivery, denial of service, etc. all targeted through geolocation, or specific networks of people.
Considering this serious threat, we believe U.S. telecommunications companies should be required to have greater transparency and explain how they are protecting the public from hacking attacks of this nature. For example, this could include providing an estimate of how many U.S. customers have received these “spam” calls, perhaps based on the known source telephone numbers being used. This would build awareness with the public about the
seriousness of this issue while providing researchers and lawmakers with more precise data about the scale of these intrusions. We also believe they should provide more specifics about how they protect from a sophisticated nation-state adversary who could combine these various flaws and weaknesses to gain unauthorized surveillance on specific targets, such as activists, journalists and government officials.
We have included below a brief chart explaining the potential attack sequence and technical detail and are happy to explain in further detail, if you are interested in learning more.
Sincerely,
Lhadon Tethong, Director, Tibet Action Institute
Nathan Freitas, Director of Technology, Tibet Action Institute
Affiliate, Berkman-Klein Center, Harvard
Cc: Senator Ed Markey
Senator Elizabeth Warren
Congressman Mike Capuano
Congressman Joe Kennedy III
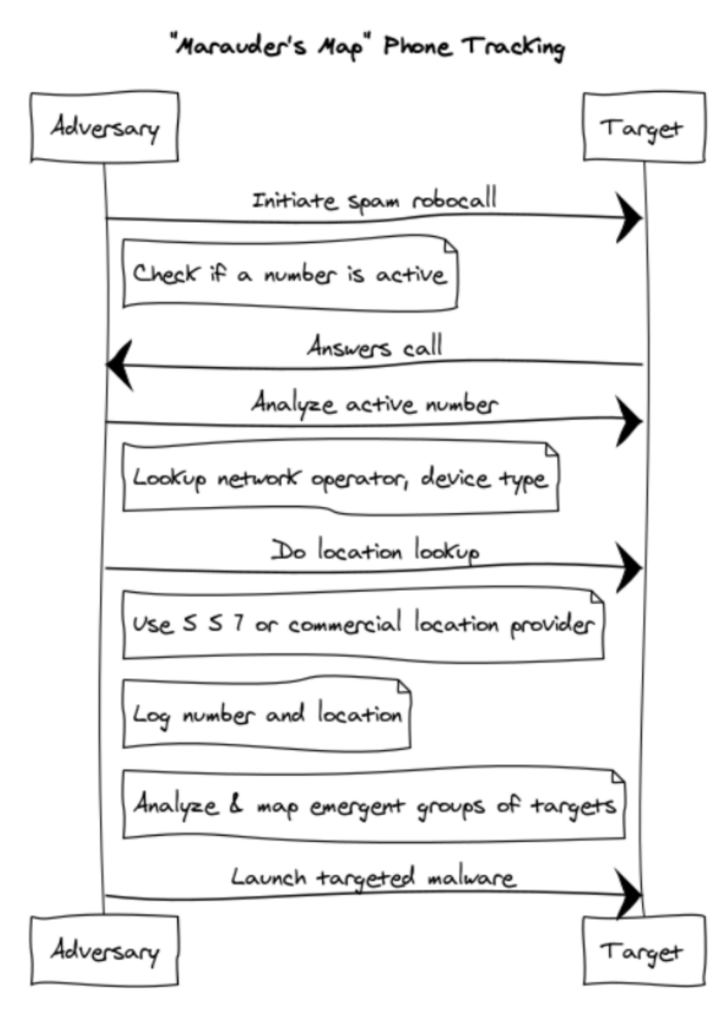
1) Initiate spam robocall to check if a number is live,
see if the user answers, responds.
2) Using that call, discover if it is a mobile device,
what network, operator it is on, etc.
3) Using either SS7 or a commercial location
provider like Securus/C3/LocationSmart look up the
location of that user
4) Log that geomapped phone for future ops,
malware delivery, tracking, etc; Continue logging
location as possible, necessary
5) Analyze the data to discover emergent groups of
people at similar places, similar times, as is known to
be done by mobile operators, advertisers, and
national security organizations.
6) With these new sets of related numbers, repeat #1
all over again, to expand your set of targets.
7) Congratulations, you’ve built the Marauders Map
for the world.
(http://harrypotter.wikia.com/wiki/Marauder%27s_Ma
p)




Leave a Reply